Implementing and Using Custom Intel SGX Trusted Library 2
Table of Contents
In the previous post, I showed how to link a trusted function that can be called insdie the enclave.
However, Intel SGX provides a way to import EDL to make a library have an ECALL. The post from Intel is [here].
1. Implementing a trusted SGX library #
As we do in the previous post, make a trusted library.
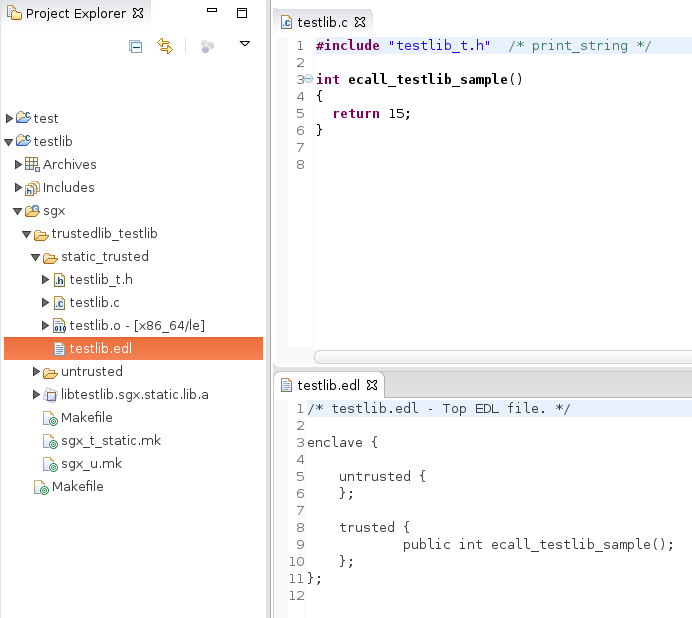
So our simple trusted SGX library has a function named ecall_testlib_sample. Let’s call this function from user space application, but outside an enclave.
2. Importing an EDL file #
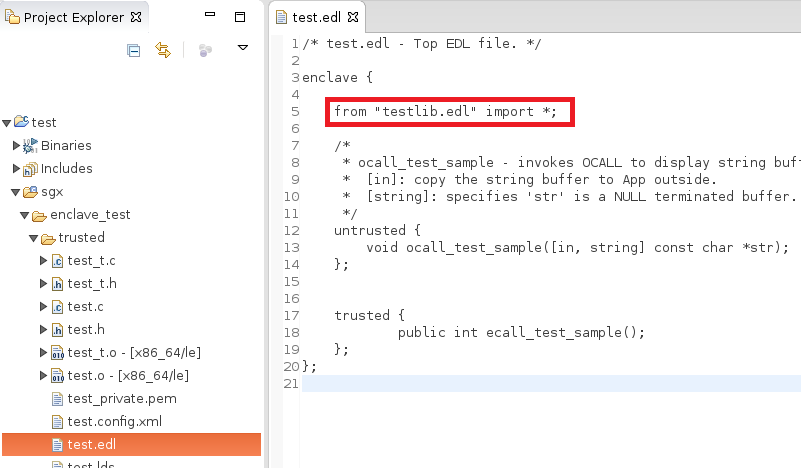
The most important thing is to import a trusted library’s EDL, as explained in the Intel’s post.
You can selectively import functions by specifying function names instead of using wildcard character.
3. Specifying search path for the imported EDL #
When building it, it says ‘cannot find testlib.edl’ in the search path. We need to add a search path to help GNU make search this EDL file.
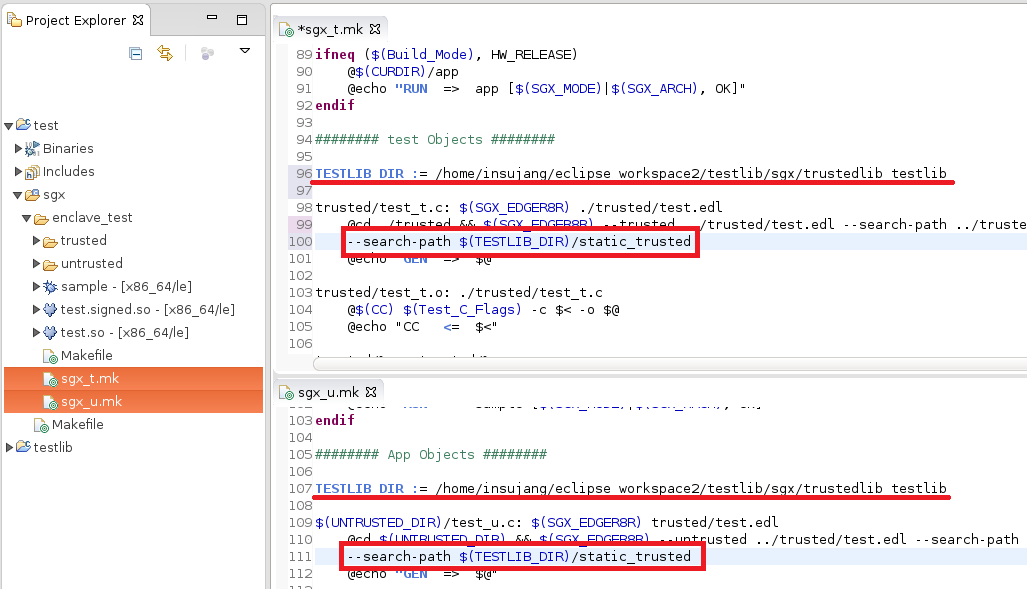
You should add search path to two Makefiles for trusted source code and untrusted one, respectively.
4. Linking a static library #
Link a built binary static trusted library into a Makefile for trusted source.
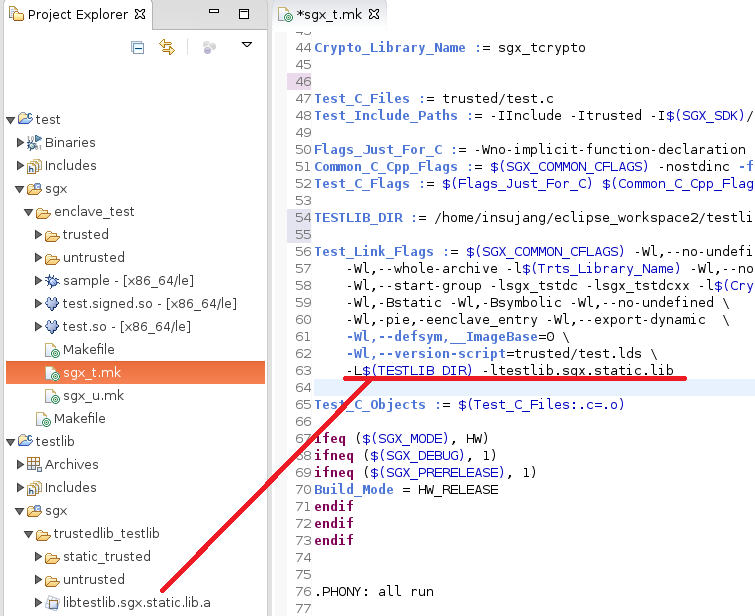
That’s it. Build your application and test whether it works.
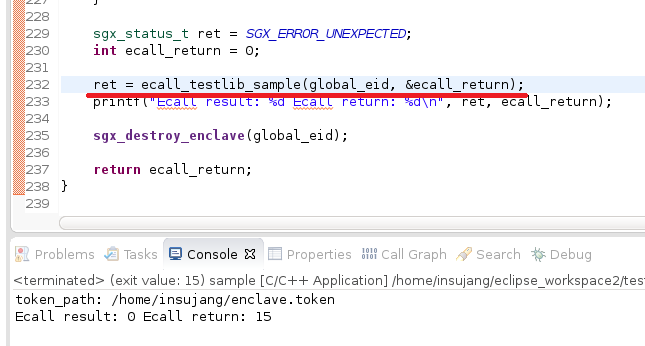
A ECALL function from the library is successfully called.